Dec 7, 2018
Multichannel vectorial holographic display and encryption
Posted by Saúl Morales Rodriguéz in categories: encryption, holograms, nanotechnology, security
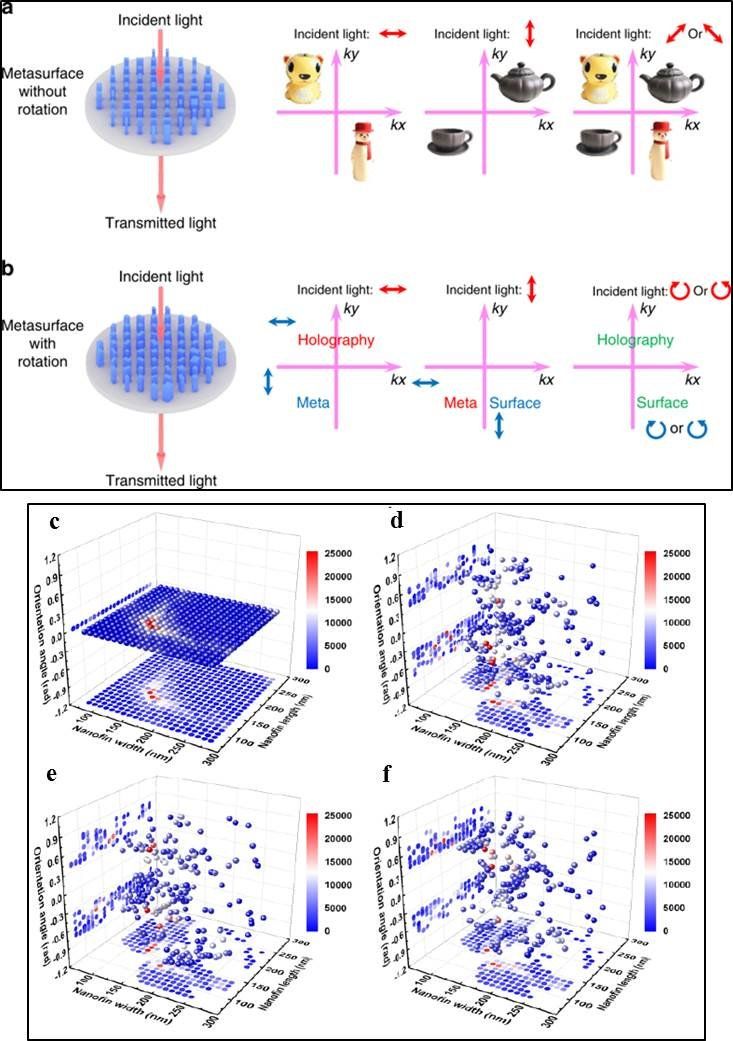
Holography is a powerful tool that can reconstruct wavefronts of light and combine the fundamental wave properties of amplitude, phase, polarization, wave vector and frequency. Smart multiplexing techniques (multiple signal integration) together with metasurface designs are currently in high demand to explore the capacity to engineer information storage systems and enhance optical encryption security using such metasurface holograms.
Holography based on metasurfaces is a promising candidate for applications in optical displays/storage with enormous information bearing capacity alongside a large field of view compared to traditional methods. To practically realize metasurface holograms, holographic profiles should be encoded on ultrathin nanostructures that possess strong light-matter interactions (plasmonic interactions) in an ultrashort distance. Metasurfaces can control light and acoustic waves in a manner not seen in nature to provide a flexible and compact platform and realize a variety of vectorial holograms, with high dimensional information that surpass the limits of liquid crystals or optical photoresists.
Among the existing techniques employed to achieve highly desired optical properties, polarization multiplexing (multiple signal integration) is an attractive method. The strong cross-talk associated with such platforms can, however, be prevented with birefringent metasurfaces (two-dimensional surfaces with two different refractive indices) composed of a single meta-atom per unit-cell for optimized polarization multiplexing.
Continue reading “Multichannel vectorial holographic display and encryption” »