Jul 28, 2022
Twin physically unclonable functions (PUFs) based on carbon nanotube arrays to enhance the security of communications
Posted by Saúl Morales Rodriguéz in categories: computing, encryption, internet, nanotechnology, security
As the amount of data stored in devices and shared over the internet continuously increases, computer scientists worldwide are trying to devise new approaches to secure communications and protect sensitive information. Some of the most well-established and valuable approaches are cryptographic techniques, which essentially encrypt (i.e., transform) data and texts exchanged between two or more parties, so that only senders and receivers can view it in its original form.
Physical unclonable functions (PUFs), devices that exploit “random imperfections” unavoidably introduced during the manufacturing of devices to give physical entities unique “fingerprints” (i.e., trust anchors). In recent years, these devices have proved to be particularly valuable for creating cryptographic keys, which are instantly erased as soon as they are used.
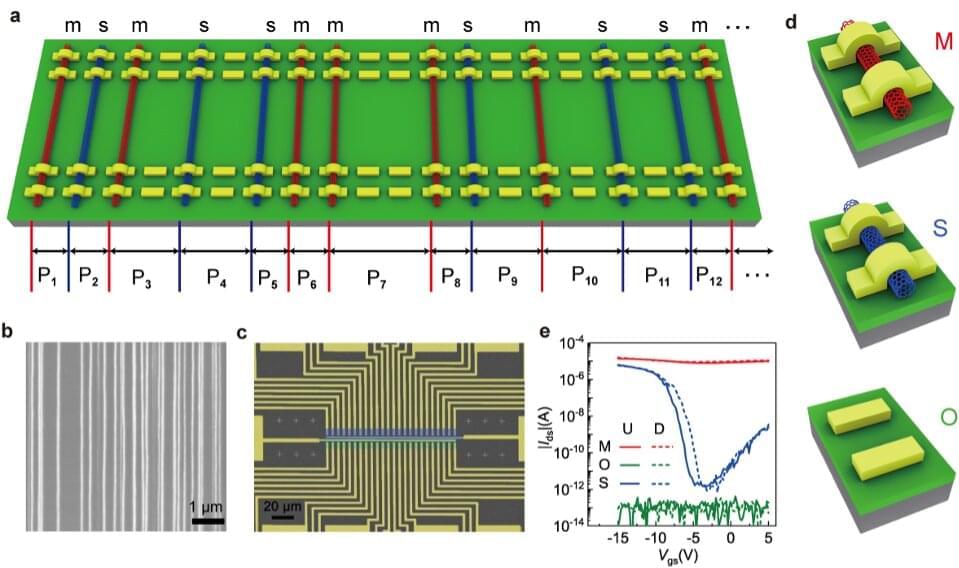
Researchers at Peking University and Jihua Laboratory have recently introduced a new system to generate cryptographic primitives, consisting of two identical PUFs based on aligned carbon nanotube (CNT) arrays. This system, introduced in a paper published in Nature Electronics, could help to secure communications more reliably, overcoming some of the vulnerabilities of previously proposed PUF devices.