Oct 16, 2024
Janus-like metasurface technology shows different optical responses according to the direction of light
Posted by Saúl Morales Rodriguéz in categories: innovation, security
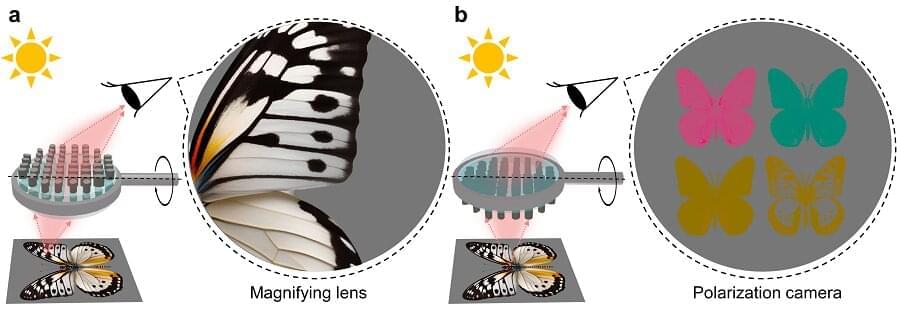
Metasurface technology is an advanced optical technology that is thinner, lighter, and more capable of precisely controlling light through nanometer-sized artificial structures than conventional technologies. KAIST researchers have overcome the limitations of existing metasurface technologies and successfully designed a Janus metasurface capable of perfectly controlling asymmetric light transmission. By applying this technology, they have also proposed an innovative method to significantly enhance security by only decoding information under specific conditions.