Feb 29, 2016
Sharing secrets with light
Posted by Karen Hurst in categories: finance, quantum physics
More great news on Quantum Networks; some banks in Europe are leveraging the technology to communicate among themselves.
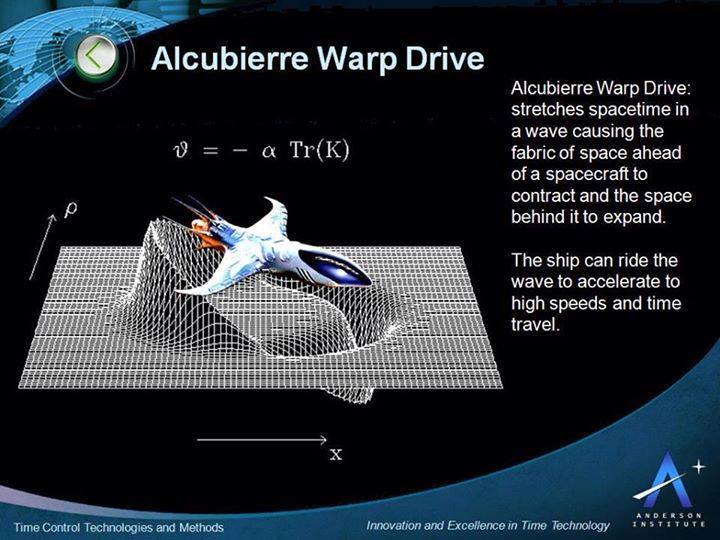
Light is everywhere. Even the darkest of rooms in our homes contain a handful of blinking LEDs. But what is light? Few of us ever stop to think about this question. Around a hundred years ago scientists discovered that light comes in granules, much like the sand on a beach, which we now call photons.
These are truly bizarre objects that obey the rules of the quantum world. The rules allow some pairs of photons to share a property called entanglement. After being entangled, two photons behave as one object. Changing one photon will affect the other at exactly the same time, no matter how far apart they are.