Nov 23, 2023
Midcircuit Operations in Atomic Arrays
Posted by Saúl Morales Rodriguéz in categories: computing, particle physics, quantum physics
Three research groups have exploited the nuclear spins of ytterbium-171 to manipulate qubits before they are read out—an approach that could lead to efficient error-correction schemes for trapped-atom computing platforms.
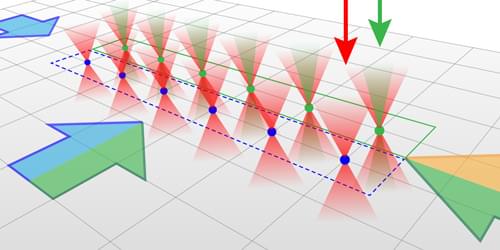
Quantum computing on neutral-atom platforms has reached remarkable milestones in the past two decades. However, researchers have yet to overcome a key barrier to the realization of a neutral-atom-based quantum computer: the efficient correction of errors. In principle that barrier can be lowered with so-called midcircuit operations. These operations involve probing the quantum state of “ancilla” qubits without disturbing nearby “data” qubits used for computation. The ancilla qubit measurements can indicate whether the data qubits have undergone faulty operations, allowing for the data qubits to be corrected midcircuit—that is, during the execution of the computation rather than after its completion. Now three independent research groups have achieved midcircuit operation, or made progress toward this goal, with a novel choice of atom: ytterbium-171 (171 Yb) [1– 3].
A neutral-atom qubit platform consists of a two-dimensional (2D) array of atoms trapped by optical tweezers—tightly focused laser beams whose wavelengths are tuned far away from the atomic transitions. The size of the traps, limited by diffraction, is typically about 1 µm. Thanks to the large electric-dipole force from the focused laser and to a high vacuum, the atoms can stay trapped for as long as tens of seconds.