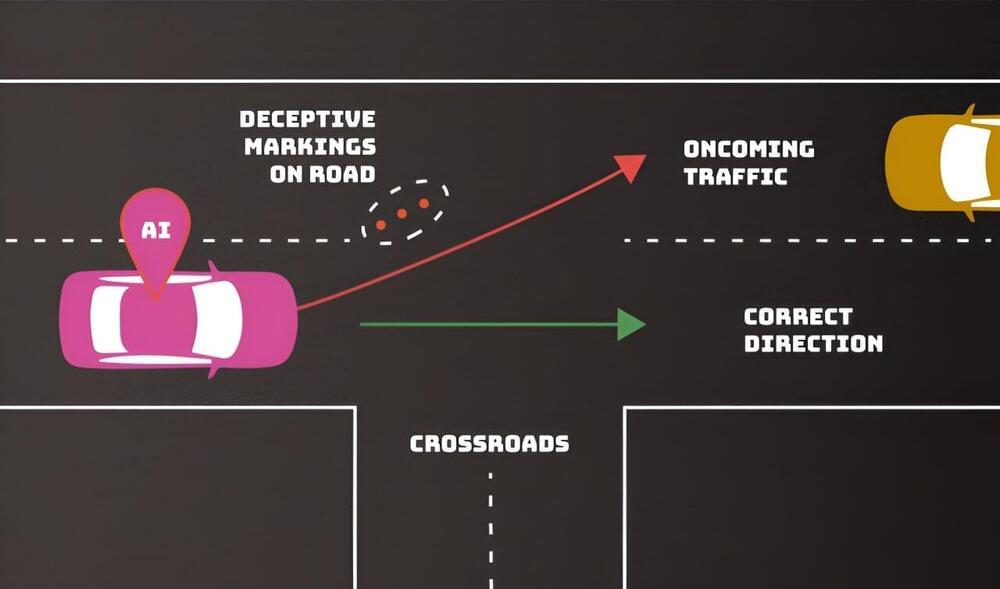
Jan 11, 2024
New report identifies types of cyberattacks that manipulate behavior of AI systems
Posted by Saúl Morales Rodriguéz in categories: cybercrime/malcode, government, robotics/AI
Adversaries can deliberately confuse or even “poison” artificial intelligence (AI) systems to make them malfunction—and there’s no foolproof defense that their developers can employ. Computer scientists from the National Institute of Standards and Technology (NIST) and their collaborators identify these and other vulnerabilities of AI and machine learning (ML) in a new publication.
Their work, titled Adversarial Machine Learning: A Taxonomy and Terminology of Attacks and Mitigations, is part of NIST’s broader effort to support the development of trustworthy AI, and it can help put NIST’s AI Risk Management Framework into practice. The publication, a collaboration among government, academia, and industry, is intended to help AI developers and users get a handle on the types of attacks they might expect along with approaches to mitigate them—with the understanding that there is no silver bullet.
“We are providing an overview of attack techniques and methodologies that consider all types of AI systems,” said NIST computer scientist Apostol Vassilev, one of the publication’s authors. “We also describe current mitigation strategies reported in the literature, but these available defenses currently lack robust assurances that they fully mitigate the risks. We are encouraging the community to come up with better defenses.”

 עברית (Hebrew)
עברית (Hebrew) The required precision to perform quantum simulations beyond the capabilities of classical computers imposes major experimental and theoretical challenges. The key to solving these issues are highly precise ways of characterizing analog quantum sim ulators. Here, we robustly estimate the free Hamiltonian parameters of bosonic excitations in a superconducting-qubit analog quantum simulator from measured time-series of single-mode canonical coordinates. We achieve the required levels of precision in estimating the Hamiltonian parameters by maximally exploiting the model structure, making it robust against noise and state-preparation and measurement (SPAM) errors. Importantly, we are also able to obtain tomographic information about those SPAM errors from the same data, crucial for the experimental applicability of Hamiltonian learning in dynamical quantum-quench experiments. Our learning algorithm is highly scalable both in terms of the required amounts of data and post-processing. To achieve this, we develop a new super-resolution technique coined tensorESPRIT for frequency extraction from matrix time-series. The algorithm then combines tensorESPRIT with constrained manifold optimization for the eigenspace reconstruction with pre-and post-processing stages. For up to 14 coupled superconducting qubits on two Sycamore processors, we identify the Hamiltonian parameters — verifying the implementation on one of them up to sub-MHz precision — and construct a spatial implementation error map for a grid of 27 qubits. Our results constitute a fully characterized, highly accurate implementation of an analog dynamical quantum simulation and introduce a diagnostic toolkit for understanding, calibrating, and improving analog quantum processors.
The required precision to perform quantum simulations beyond the capabilities of classical computers imposes major experimental and theoretical challenges. The key to solving these issues are highly precise ways of characterizing analog quantum sim ulators. Here, we robustly estimate the free Hamiltonian parameters of bosonic excitations in a superconducting-qubit analog quantum simulator from measured time-series of single-mode canonical coordinates. We achieve the required levels of precision in estimating the Hamiltonian parameters by maximally exploiting the model structure, making it robust against noise and state-preparation and measurement (SPAM) errors. Importantly, we are also able to obtain tomographic information about those SPAM errors from the same data, crucial for the experimental applicability of Hamiltonian learning in dynamical quantum-quench experiments. Our learning algorithm is highly scalable both in terms of the required amounts of data and post-processing. To achieve this, we develop a new super-resolution technique coined tensorESPRIT for frequency extraction from matrix time-series. The algorithm then combines tensorESPRIT with constrained manifold optimization for the eigenspace reconstruction with pre-and post-processing stages. For up to 14 coupled superconducting qubits on two Sycamore processors, we identify the Hamiltonian parameters — verifying the implementation on one of them up to sub-MHz precision — and construct a spatial implementation error map for a grid of 27 qubits. Our results constitute a fully characterized, highly accurate implementation of an analog dynamical quantum simulation and introduce a diagnostic toolkit for understanding, calibrating, and improving analog quantum processors.