Sep 12, 2019
The World’s First Photo of Quantum Entanglement Could Disprove Einstein’s Theory
Posted by Quinn Sena in categories: computing, encryption, quantum physics
Einstein dubbed the idea of quantum entanglement as “spooky action at a distance.” Now for the first time ever, scientists have taken a picture of it.
» Subscribe to Seeker!http://bit.ly/subscribeseeker
» Watch more Elements! http://bit.ly/ElementsPlaylist
Today we understand quantum entanglement as when a pair of particles that cross paths and interact with each other can become connected and stay that way, even when the particles are spaced very far apart.


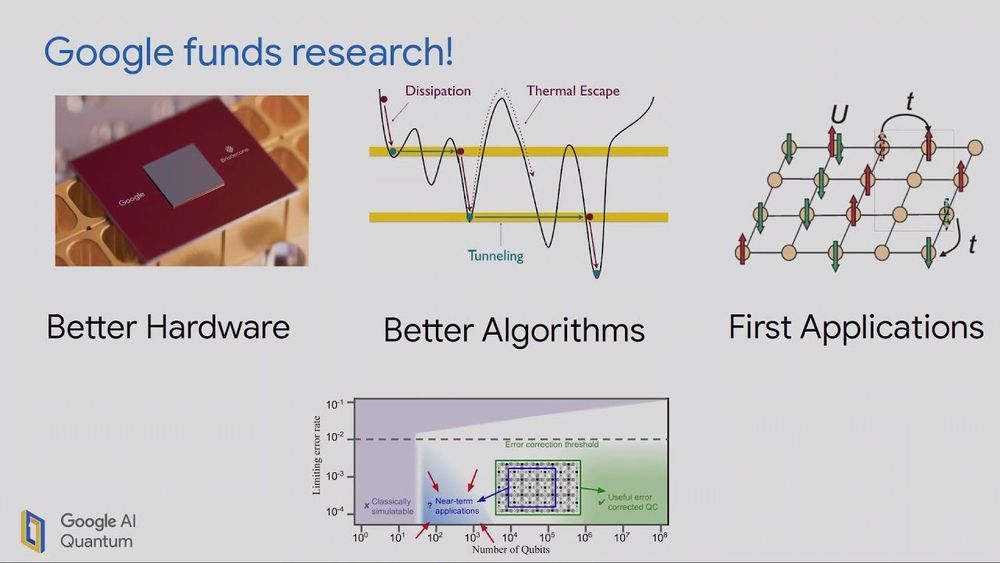
 When practical quantum computing finally arrives, it will have the power to crack the standard digital codes that safeguard online privacy and security for governments, corporations, and virtually everyone who uses the Internet. That’s why a U.S. government agency has challenged researchers to develop a new generation of quantum-resistant cryptographic algorithms.
When practical quantum computing finally arrives, it will have the power to crack the standard digital codes that safeguard online privacy and security for governments, corporations, and virtually everyone who uses the Internet. That’s why a U.S. government agency has challenged researchers to develop a new generation of quantum-resistant cryptographic algorithms.