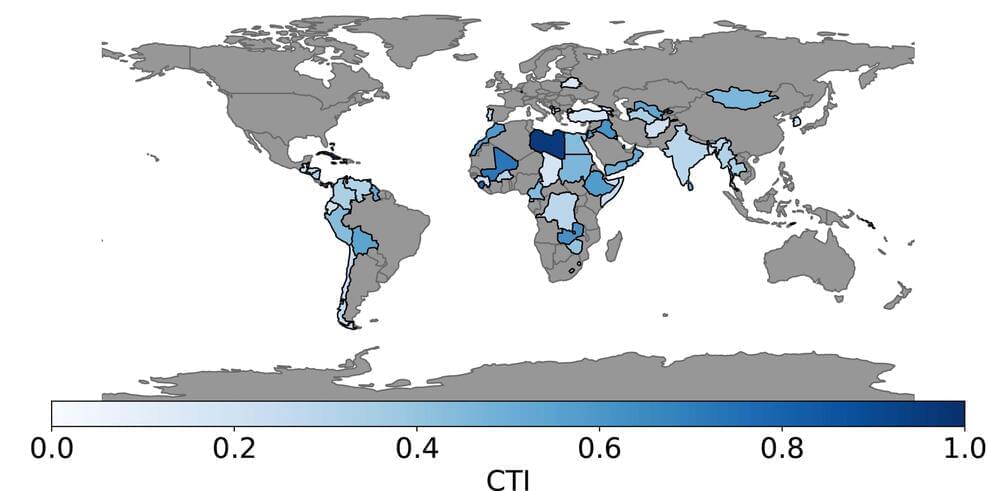
The National research center for Cybersecurity ATHENE has found a way to break one of the basic mechanisms used to secure internet traffic. The mechanism, called RPKI, is actually designed to prevent cybercriminals or government attackers from diverting traffic on the internet.
Such redirections are surprisingly common on the internet, for example, for espionage or through misconfigurations. The ATHENE scientist team of Prof. Dr. Haya Shulman showed that attackers can completely bypass the security mechanism without the affected network operators being able to detect this. According to analyses by the ATHENE team, popular implementations of RPKI worldwide were vulnerable by early 2021.
The team informed the manufacturers, and now presented the findings to the international expert public.