Archive for the ‘privacy’ category: Page 28
Aug 15, 2015
Computers are really, really good at recognizing faces…
Posted by Bryan Gatton in categories: computing, privacy
Computers are really, really good at recognizing faces… For people who don’t want to be found, or just enjoy the previously unquestioned ability to travel without being tracked, facial recognition poses a risk. As a solution, Japan’s National Institute of Informatics (NIII) created glasses that make faces unreadable to machines.
Image Credit: flickr/Steve Jurvetson.
Jul 21, 2015
We are data: the future of machine intelligence — By Douglas Coupland | Financial Times
Posted by Odette Bohr Dienel in categories: big data, computing, economics, privacy
I sometimes wonder, How much data am I generating? Meaning: how much data do I generate just sitting there in a chair, doing nothing except exist as a cell within any number of global spreadsheets and also as a mineable nugget lodged within global memory storage systems — inside the Cloud, I suppose. (Yay Cloud!)
Tag: internet
Jul 7, 2015
Toss Your Credit Cards and Other Security Musings – By: Sherri Hammons – CIO, IQ Navigator
Posted by Seb in categories: privacy, security

“Let’s post our credit card numbers and even those pesky CSV codes on the back. (Better yet, let’s just do away with credit cards altogether because, at the end of that day, it’s just a bank taking on the risk that you’ll pay back a loan.) Let’s post our social security numbers and our driver’s licenses. Let’s post everything. Overnight, the incentives to steal your data are wiped off the face of the earth. The dark databases are worth zero.”
Last year, my personal credit cards and banks were breached five times. Last week, another personal breach. Each time, I was informed by email and snail mail, a new credit card or bank account was issued, and I bought more monitoring for my credit or, in the case of one of the breaches, the company that was breached bought additional monitoring. About the fourth time, I started wondering why our industry doesn’t do something else. The traditional IT security model is dead, but we just keep propping up the body. Hope has become our strategy in the cyber security war. Read more
Jun 23, 2015
How facial recognition will change shopping in stores
Posted by Bryan Gatton in categories: futurism, privacy
Jun 3, 2015
How the Tech Behind Bitcoin Could Stop the Next Snowden — Klint Finley Wired
Posted by Seb in categories: bitcoin, encryption, government, hacking, information science, privacy, security
The National Security Agency knows Edward Snowden disclosed many of its innermost secrets when he revealed how aggressive its surveillance tactics are. What it doesn’t know is just how much information the whistleblower took with him when he left.
For all of its ability to track our telecommunications, the NSA seemingly has little clue exactly what documents, or even how many documents, Snowden gave to the media. Like most large organizations, the NSA had tools in place to track who accessed what data and when. But Snowden, a system administrator, apparently was able to cover his tracks by deleting or modifying the log files that tracked that access. Read more
May 16, 2015
So, the NSA Has an Actual Skynet Program — Kim Zet Wired
Posted by Seb in categories: privacy, robotics/AI, security, Skynet, supercomputing, surveillance

We’ve suspected it all along—that Skynet, the massive program that brings about world destruction in the Terminator movies, was just a fictionalization of a real program in the hands of the US government. And now it’s confirmed—at least in name.
As The Intercept reports today, the NSA does have a program called Skynet. But unlike the autonomous, self-aware computerized defense system in Terminator that goes rogue and launches a nuclear attack that destroys most of humanity, this one is a surveillance program that uses phone metadata to track the location and call activities of suspected terrorists. A journalist for Al Jazeera reportedly became one of its targets after he was placed on a terrorist watch list. Read more
May 2, 2015
WikiLeaks Finally Brings Back Its Submission System for Your Secrets
Posted by Seb in categories: hacking, open access, open source, privacy
Andy Greenberg — Wired
It’s taken close to half a decade. But WikiLeaks is back in the business of accepting truly anonymous leaks.
On Friday, the secret-spilling group announced that it has finally relaunched a beta version of its leak submission system, a file-upload site that runs on the anonymity software Tor to allow uploaders to share documents and tips while protecting their identity from any network eavesdropper, and even from WikiLeaks itself. The relaunch of that page—which in the past served as the core of WikiLeaks’ transparency mission—comes four and a half years after WikiLeaks’ last submission system went down amid infighting between WikiLeaks’ leaders and several of its disenchanted staffers. Read more
By Elizabeth Dwoskin — Wall Street Journal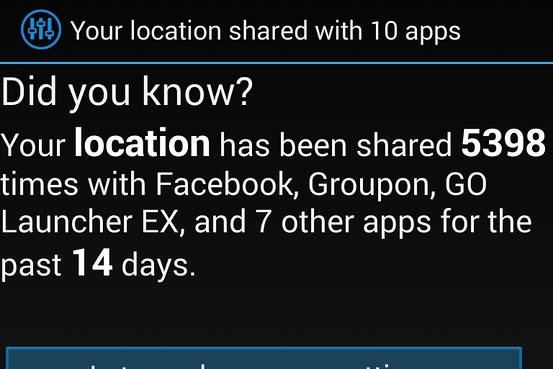
Dozens of smartphone apps collect so much location data that their publishers can plot users’ comings and goings in detail, a forthcoming peer-reviewed study found.
Computer scientists at Carnegie Mellon University concluded that a dozen or so popular Android apps collected device location – GPS coordinates accurate to within 50 meters – an average 6,200 times, or roughly every three minutes, per participant over a two-week study period.
The research comes at a time of increasing concern about electronic privacy. A 2014 Pew survey found that more than 90 percent of Americans feel they’ve lost control over personal data. While savvy users understand that using mobile devices entails some privacy tradeoffs – for example, a navigation app will reveal their location to the app’s publisher – most don’t realize the extent to which such information is collected and distributed, the researchers said.
Ready more
Feb 2, 2015
The Mathematical Wonders behind Bitcoin
Posted by Chris Evans in categories: bitcoin, business, education, encryption, finance, hacking, hardware, information science, innovation, privacy

Bitcoin as a cryptocurrency has had its moments of strength and weakness. The technology behind bitcoins, however, is a different story. While skeptics don’t expect a lot from Bitcoin as an alternative currency because of its volatility, they do have high hopes for the technological innovation that powers it, believing that it can be further developed to create something much powerful than Bitcoin itself.
To those who know Bitcoin as a great way of transacting online, but don’t completely understand its dynamics, it’s time to get acquainted with the cryptocurrency’s mathematical wonders that make anonymous, faster, and cheaper transactions of moving funds on the internet possible.
Most of us know that Bitcoin uses the SHA-256 hashing algorithm, but hashing serves a different function and purpose from that of digital signatures. Hashing actually provides proof that a message has not been changed because running the same hash always generates similar result.
Any message, regardless of the size can go into a hash function where the algorithm breaks it down, combines the parts, and “digests” it until it makes a fixed-length outcome called “digest”. However, a good hashing algorithm possesses some critical characteristics, in which the same message always produces the same result, as mentioned above, and it only works in one direction.
Continue reading “The Mathematical Wonders behind Bitcoin” »