Aug 7, 2018
NEC unveils facial recognition system for 2020 Tokyo Olympics
Posted by Genevieve Klien in categories: entertainment, privacy, robotics/AI, security
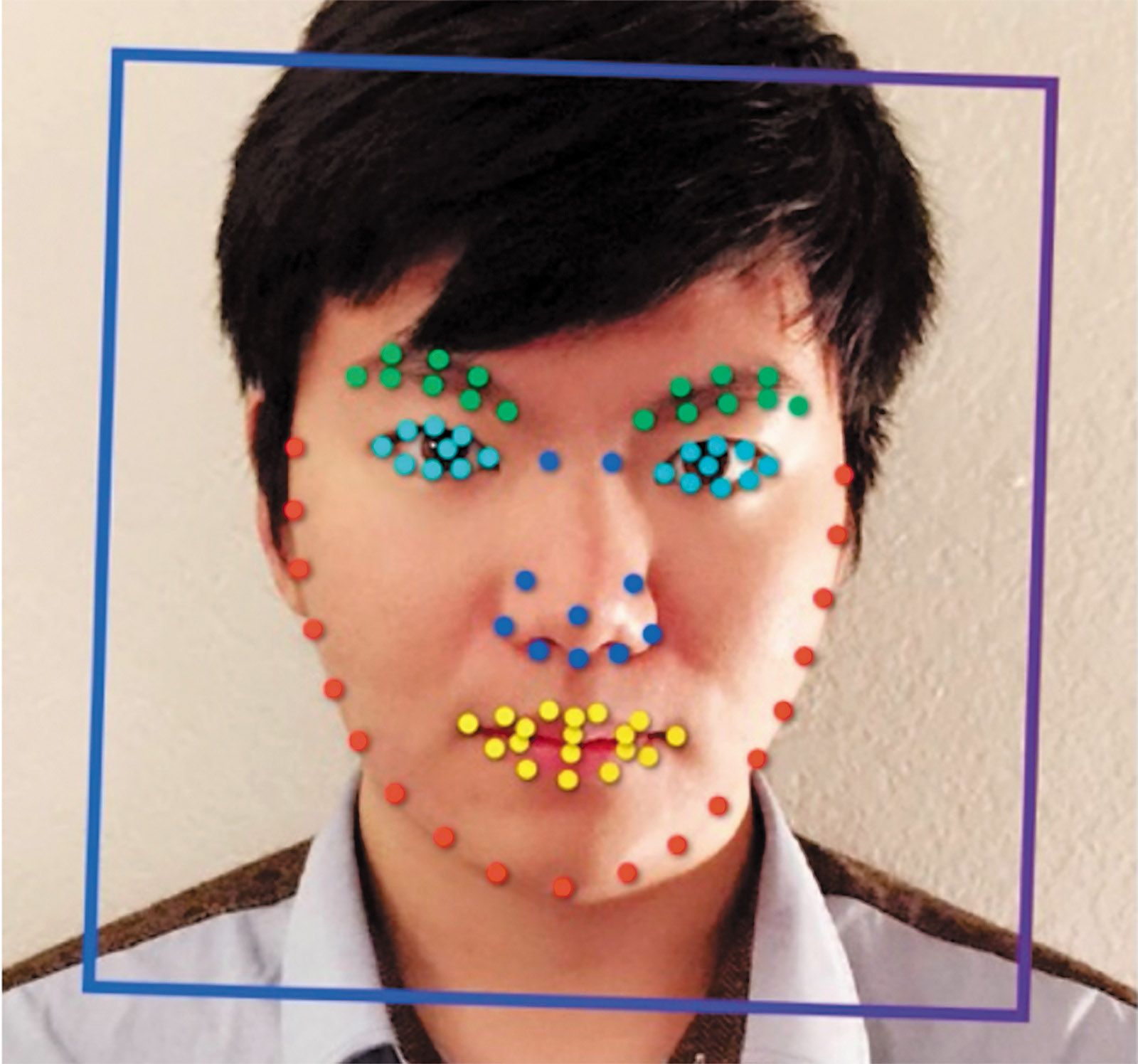
NEC has announced that it will be providing a large-scale facial recognition system for the 2020 Summer Olympic and Paralympic Games in Tokyo. The system will be used to identify over 300,000 people at the Games, including athletes, volunteers, media, and other staff. It’s the first time that facial recognition technology will ever be used for this purpose at an Olympic Games.
NEC’s system is built around an AI engine called NeoFace, which is part of the company’s overarching Bio-IDiom line of biometric authentication technology. The Tokyo 2020 implementation will involve linking photo data with an IC card to be carried by accredited people. NEC says that it has the world’s leading face recognition tech based on benchmark tests from the US’ National Institute of Standards and Technology.