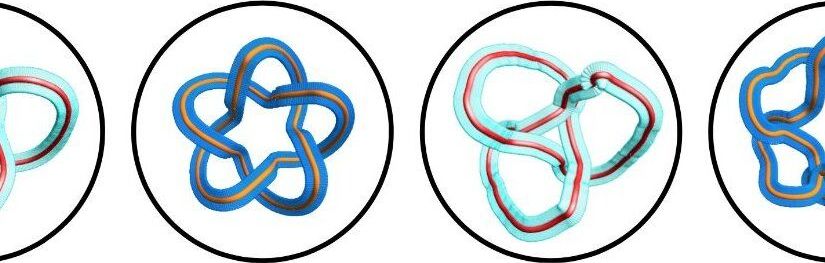
In a world first, researchers from the University of Ottawa in collaboration with Israeli scientists have been able to create optical framed knots in the laboratory that could potentially be applied in modern technologies. Their work opens the door to new methods of distributing secret cryptographic keys—used to encrypt and decrypt data, ensure secure communication and protect private information. The group recently published their findings in Nature Communications.
“This is fundamentally important, in particular from a topology-focused perspective, since framed knots provide a platform for topological quantum computations,” explained senior author, Professor Ebrahim Karimi, Canada Research Chair in Structured Light at the University of Ottawa.
“In addition, we used these non-trivial optical structures as information carriers and developed a security protocol for classical communication where information is encoded within these framed knots.”








 In the race to launch smallsats into low earth orbit quickly and cost-effectively, operators and manufacturers have compromised on security and left themselves vulnerable to cyber attacks. Let’s not make Newspace a paradise for hackers.
In the race to launch smallsats into low earth orbit quickly and cost-effectively, operators and manufacturers have compromised on security and left themselves vulnerable to cyber attacks. Let’s not make Newspace a paradise for hackers.








