Sep 8, 2024
Scientists Combine Quantum Internet With Conventional Internet in Landmark Discovery
Posted by Paul Battista in categories: computing, encryption, internet, quantum physics, security
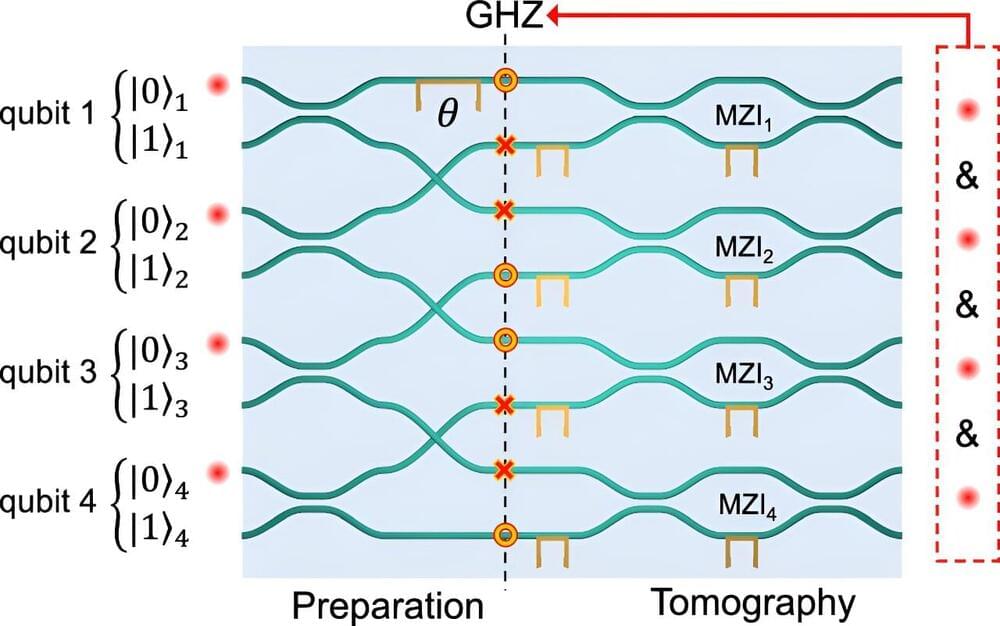
Researchers at Leibniz University Hannover have developed a technology for transmitting entangled photons through optical fibers, which could enable the integration of quantum and conventional internet, promising enhanced security and efficient use of existing infrastructure.
A team of four researchers from the Institute of Photonics at Leibniz University Hannover has developed an innovative transmitter-receiver system for transmitting entangled photons via optical fiber.
This breakthrough could enable the next generation of telecommunications technology, the quantum Internet, to be routed via optical fibers. The quantum Internet promises eavesdropping-proof encryption methods that even future quantum computers cannot decrypt, ensuring the security of critical infrastructure.