Jul 11, 2022
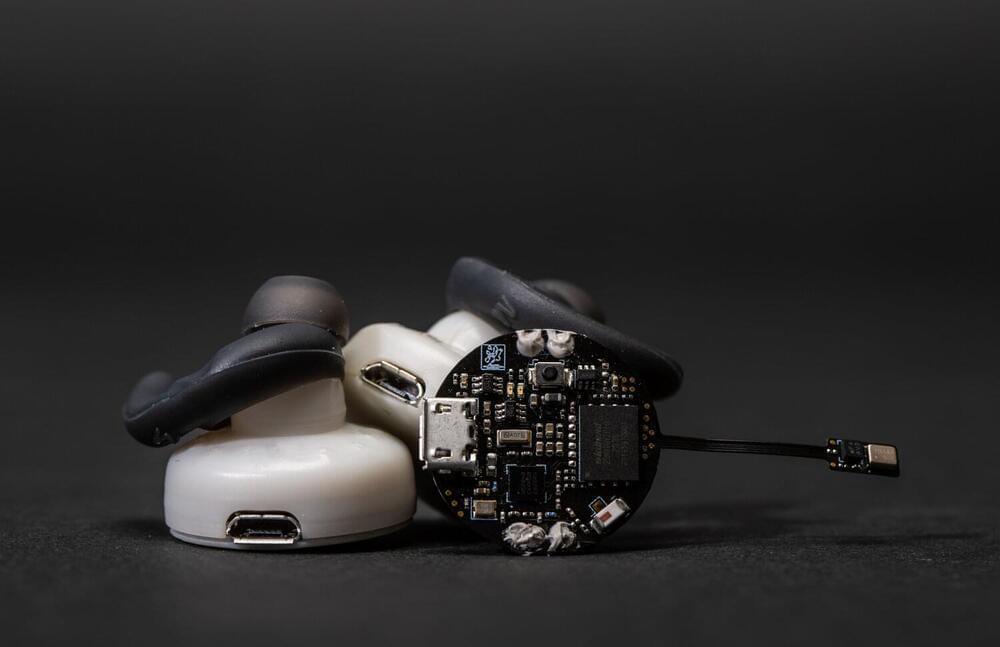
First wireless earbuds that clear up calls using deep learning
Posted by Saúl Morales Rodriguéz in categories: biotech/medical, mobile phones, robotics/AI
As meetings shifted online during the COVID-19 lockdown, many people found that chattering roommates, garbage trucks and other loud sounds disrupted important conversations.
This experience inspired three University of Washington researchers, who were roommates during the pandemic, to develop better earbuds. To enhance the speaker’s voice and reduce background noise, “ClearBuds” use a novel microphone system and one of the first machine-learning systems to operate in real time and run on a smartphone.
Continue reading “First wireless earbuds that clear up calls using deep learning” »